
Two pirate IPTV services have become the latest victims in a growing line of services to be hacked by malicious actors. The platforms, which appear to be linked, have been ordered to pay a bitcoin ransom of around US$94,000. There is also a live threat to email customer data and banking information to the police and anti-piracy groups.
In most countries blackmail is a very serious offense resulting in considerable jail sentences.
However, that is proving no deterrent to an individual behind a series of hacks targeting pirate IPTV providers over the past couple of years.
Two Linked Suppliers Targeted in New Hacks
During the past two days, a pair of UK-based IPTV suppliers – SapphireSecure.net and KS-Hosting.com – became victims in what appears to be a series of hacks carried out by the same individual. Apparently connected by ownership, the platforms went down and began displaying similar messages on their homepages indicating that they had been seriously compromised.
The messages that appeared on both sites are similar and it seems from the timing that SapphireSecure was taken down first, displaying a “Down for Maintenance” error and the following text.
“Your IPTV provider from [redacted] in the United Kingdom has not secured your details and put you at huge risk. All the databases will be shared with the police and copyright protection agencies and posted online shortly.
[Name redacted] has the option to still protect his customers and himself and stop this and there are two ways of him doing this, this is his choice and likely depends on how much he cares about his customers data.”
The message on KS-Hosting goes a step further, again naming the individual allegedly behind both platforms while providing information relating to his current address, former address, and even his ISP. It also follows up with a threat to leak the personal information of staff members.
Considerable Ransom Demands
In common with previous attacks against IPTV providers, these IPTV brands (which appear to have the same underlying service) are being ordered to pay a bitcoin ransom to prevent the above threats being carried out. The amount is 2 BTC, which at current rates is around US$94,000, although it is not entirely clear whether this amount has to be paid overall or for each site hacked.
According to the hacker, the bitcoin demanded has been balanced to account for the amount of money generated by the service(s), with 2 BTC estimated as less than two weeks’ revenue.
“[H]e has stolen huge amounts of revenue from broadcasters and the content that he steals he does not give away for free he profits from this so we are stealing from the thief [sic],” the announcement reads.
Alternative Way To Appease The Hacker
Strangely, the hacker also gives the owner of both SapphireSecure.net and KS-Hosting.com a way out without having to pay a ransom. The demand is for the services to completely shut down, with no chance of a resurrection, while refunding money back to subscribers to compensate them for their lack of service, “as this is not their fault.”
On the surface, the demands seem somewhat contradictory. If the owner of the platforms doesn’t pay, then customers will be punished. However, if he pays or shuts down they will not, since this is not their fault. It appears, therefore, that as long as the services’ operator is punished financially, that will be considered enough not to punish the customers. This is painted as the owners’ choice but quite obviously, he didn’t set those terms.
No Ransom Paid – Yet
While some believe bitcoin is the holy grail of anonymous payments, transactions for a bitcoin wallet are public information and if we take a look at the hacker’s wallet (which may have been set up for this purpose alone) we can see that no ransom has been paid.
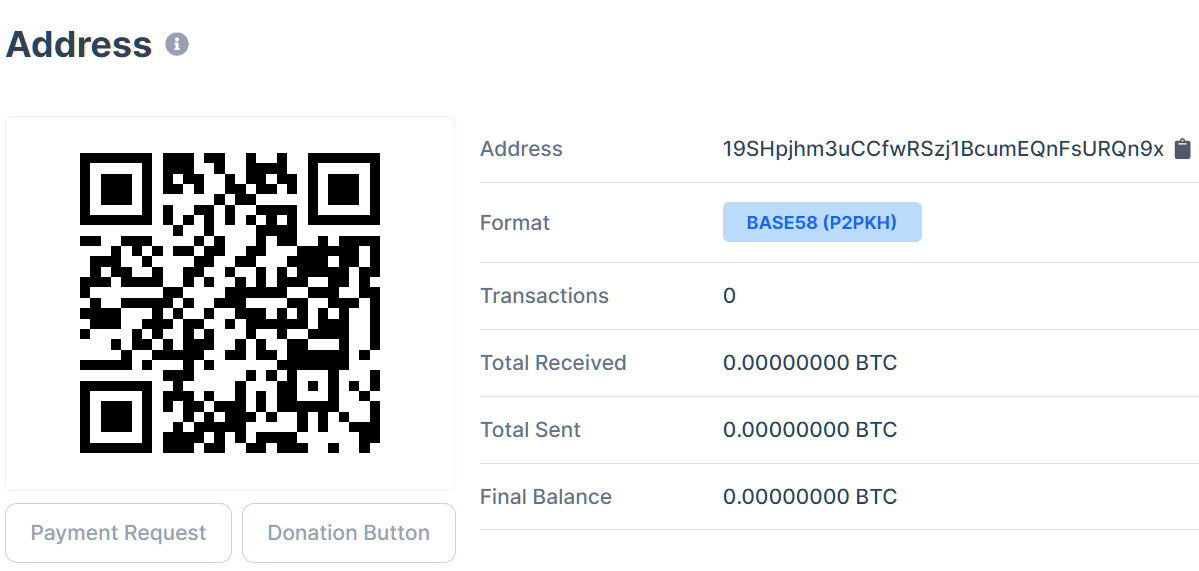
Blackmailing people who are already on the wrong side of the law could be an effective way to encourage payment but anecdotal evidence provided in relation to previous cases suggests that paying this particular hacker off doesn’t necessarily work, since he reportedly comes back for more – and more – when people pay.
The other sizeable issue in this case is that the information leaked by the hacker already seems to allow interested parties to discover who is behind both services, meaning that beyond protecting customers’ information, the damage appears to have been done, ruining any incentive to pay.
The key here, it seems, is for service operators and their customers to be more cautious when it comes to launching and/or using a pirate service. Then, when they fall victim to hacks (which are by now frequent and common knowledge), any information obtained will be of limited use. If either operates in the open, with no caution in respect of identities, then this type of blackmail will continue to prove enticing to hackers.
Source: ![]() TorrentFreak.com
TorrentFreak.com






Be the first to comment